 Reinforcement learning is a technique, common in computer science, in which a computer system learns how best to solve some problem through trial-and-error. Classic applications of reinforcement learning involve problems as diverse as robot navigation, network administration and automated surveillance.
At the Association for Uncertainty in Artificial Intelligence's annual conference this summer, researchers from MIT's Laboratory for Information and Decision Systems (LIDS) and Computer Science and Artificial Intelligence Laboratory will present a new reinforcement-learning algorithm that, for a wide range of problems, allows computer systems to find solutions much more effi
Reinforcement learning is a technique, common in computer science, in which a computer system learns how best to solve some problem through trial-and-error. Classic applications of reinforcement learning involve problems as diverse as robot navigation, network administration and automated surveillance.
At the Association for Uncertainty in Artificial Intelligence's annual conference this summer, researchers from MIT's Laboratory for Information and Decision Systems (LIDS) and Computer Science and Artificial Intelligence Laboratory will present a new reinforcement-learning algorithm that, for a wide range of problems, allows computer systems to find solutions much more effi
 This is one of those Windows characteristics which has been there in the existence since the Windows XP days. Yes, we are talking about the fact that Windows throws up a notification that it would restarting in 15 minutes.
This is one of those Windows characteristics which has been there in the existence since the Windows XP days. Yes, we are talking about the fact that Windows throws up a notification that it would restarting in 15 minutes.These are the times when your heart slips to your mouth especially when you notice that your machine has actually restarted and you failed to save your work. These are the times of anger, frustration and helplessness. If you wish to avoid such thing happening to you, then you have to follow the below steps to make sure that your Windows machine do not restart after its updates. Steps To Stop Windows From Restarting After Update  As you know what is virus and its functions. If you want to avoid download a file that may have virus attachment then do following steps:
Step 1
As you know what is virus and its functions. If you want to avoid download a file that may have virus attachment then do following steps:
Step 1Open run and type in run (gpedit.msc) without round braces it will open a local group policy now click on user configuration then click on administrative templates after this click on windows components after this double click on windows explorer. Step 2 Now double click on “Configure Outlook Express” in the right panel of local group policy. It will open a new window there are three options you will have to click on enable radio button and from options mark check box that say &ldquo  The website has been targeted by police in various countries - but still continues to operate
An "underground" website famed for selling drugs and other illegal items has been targeted in a cyberattack.
It appears the site suffered from a Distributed Denial of Service (DDoS) attack over the course of Tuesday and Wednesday.
Silk Road is only accessible through Tor, a service which allows users to browse anonymously online.
Several US politicians have called for the marketplace to be shut down, without success.
DDoS attacks involve flooding a website with more traffic than it can handle, therefore knocking it offline.
After two days of intermittent service, Silk Road'
The website has been targeted by police in various countries - but still continues to operate
An "underground" website famed for selling drugs and other illegal items has been targeted in a cyberattack.
It appears the site suffered from a Distributed Denial of Service (DDoS) attack over the course of Tuesday and Wednesday.
Silk Road is only accessible through Tor, a service which allows users to browse anonymously online.
Several US politicians have called for the marketplace to be shut down, without success.
DDoS attacks involve flooding a website with more traffic than it can handle, therefore knocking it offline.
After two days of intermittent service, Silk Road'
 If you’ve signed up for a broadband internet provider anytime in the recent past you’ll probably have received a wireless router as part of the package. In fact there’s a good chance you’ve gone through several providers and amassed a collection of routers over the years.
Wi-Fi routers were once an expensive gadget but they’re now so commonplace that it’s not worth the effort to sell them and chucking out working electronics is wasteful. So what to do?
Here are three ideas for useful things you can do with an old wireless router.
Extend the range of your wireless network
As useful as Wi-Fi can be there are factors beyond your control which can seve
If you’ve signed up for a broadband internet provider anytime in the recent past you’ll probably have received a wireless router as part of the package. In fact there’s a good chance you’ve gone through several providers and amassed a collection of routers over the years.
Wi-Fi routers were once an expensive gadget but they’re now so commonplace that it’s not worth the effort to sell them and chucking out working electronics is wasteful. So what to do?
Here are three ideas for useful things you can do with an old wireless router.
Extend the range of your wireless network
As useful as Wi-Fi can be there are factors beyond your control which can seve
 Now I am not getting into the details why would one want to disable right click button on keyboard. or infact, why would want to disable any keyboard key? Well, I am not sure about that as I am not at all interested in the answer.
I know a number of people who have asked me if there is a way to disable any specific keyboard button. So, I checked number of sites and came across few tools which would let you do this.
The first tool which I was talking about is MapKeyboard. This is actually a free tool which lets you deactivate any button you want on your keyboard.
What I have liked the most about this tool is that it is unbelievably easy to use and it is a portable utility, so it does no
Now I am not getting into the details why would one want to disable right click button on keyboard. or infact, why would want to disable any keyboard key? Well, I am not sure about that as I am not at all interested in the answer.
I know a number of people who have asked me if there is a way to disable any specific keyboard button. So, I checked number of sites and came across few tools which would let you do this.
The first tool which I was talking about is MapKeyboard. This is actually a free tool which lets you deactivate any button you want on your keyboard.
What I have liked the most about this tool is that it is unbelievably easy to use and it is a portable utility, so it does no
 Have you ever tried to track the location of email sender? Yes, it is like you receive an email and then you wish to find where exactly did this email come from.
It isn’t any FBI level task to trace email sender. We would first find the IP address of the machine from which the email was sent, and then we would track that IP address. An indirect way, but an accurate one to find out what you are looking for.
Steps To Track The Location Of Email Sender
Find Email Sender’s IP Address On Gmail
If you got an email on your Gmail account, then below are the steps to find of the sender’s IP address:
On the right hand side where you have Reply button, you will a
Have you ever tried to track the location of email sender? Yes, it is like you receive an email and then you wish to find where exactly did this email come from.
It isn’t any FBI level task to trace email sender. We would first find the IP address of the machine from which the email was sent, and then we would track that IP address. An indirect way, but an accurate one to find out what you are looking for.
Steps To Track The Location Of Email Sender
Find Email Sender’s IP Address On Gmail
If you got an email on your Gmail account, then below are the steps to find of the sender’s IP address:
On the right hand side where you have Reply button, you will a
 WASHINGTON: A flaw in commonly used applications on Android smartphones such as texting, messaging or microblogging could spread private information or allow forged fraudulent messages to be posted, a recent study has revealed.
WASHINGTON: A flaw in commonly used applications on Android smartphones such as texting, messaging or microblogging could spread private information or allow forged fraudulent messages to be posted, a recent study has revealed.University of California graduate student Dennis (Liang) Xu has identified security flaws in about 1,20,000 free apps in Android smartphones, which has about a half-billion users worldwide. The flaws start to appear just when the victim downloads a piece of malicious code onto their phone which could be hidden in a useful app, or attached to a 'phishing' e-mail or web link, that could harm the vulnerable programmes by invading the  This is definitely one of those articles which you would want to read once as you might find something really useful here. You must of heard of keylogger. Well, its a program which records your keyboard activities on your machine.
It means, when you typing your email account passwords, bank pins and other confidential stuff like that, your keyboard strokes would be getting recorded at the backend. Oh yes, its as dangerous as it sounds.
You can find many programs which can be installed manually in order to find characters that are being typed, and at the same time, such programs are also planted on your machine by hackers.
If your machine is jacked by hackers, then it isn’t e
This is definitely one of those articles which you would want to read once as you might find something really useful here. You must of heard of keylogger. Well, its a program which records your keyboard activities on your machine.
It means, when you typing your email account passwords, bank pins and other confidential stuff like that, your keyboard strokes would be getting recorded at the backend. Oh yes, its as dangerous as it sounds.
You can find many programs which can be installed manually in order to find characters that are being typed, and at the same time, such programs are also planted on your machine by hackers.
If your machine is jacked by hackers, then it isn’t e
 Yes, you read the title right. You can easily host website on Dropbox for free. Before we start with it, I would like you to check out some amazing ways to increase your Dropbox storage for free. Assuming you have not good enough storage space available on your Dropbox account, lets talk about website hosting now.
Once you are done reading this, you would surprised to know how easy it is to get free hosting from Dropbox. Ya ya, its not that Dropbox is letting you host a website by the means of any tools, but we are trying to use the Dropbox in a way that it would basically host your web pages.
How To Host Website On Dropbox For Free
Before we switch to dro
Yes, you read the title right. You can easily host website on Dropbox for free. Before we start with it, I would like you to check out some amazing ways to increase your Dropbox storage for free. Assuming you have not good enough storage space available on your Dropbox account, lets talk about website hosting now.
Once you are done reading this, you would surprised to know how easy it is to get free hosting from Dropbox. Ya ya, its not that Dropbox is letting you host a website by the means of any tools, but we are trying to use the Dropbox in a way that it would basically host your web pages.
How To Host Website On Dropbox For Free
Before we switch to dro
 Everybody love free stuff and Internet is one of the top listed items in this most loved list. And if you wish to find free WiFi hotspots, then continue reading this post. As someone smart has said, ‘its all around you, you just need to open your eyes and find it’. This thing goes quite well with finding free WiFi.
Most of us are not actually bothered much about it, or say we do not really try finding it. Sometimes scanning for WiFi networks using your default WiFi app won’t do. In this post I would be sharing some of the most amazing and fruitful ways to find WiFi hotspots for free.
3 Best Ways To Find Free WiFi HotSpots
1.) Use WeFi
Its not just about usi
Everybody love free stuff and Internet is one of the top listed items in this most loved list. And if you wish to find free WiFi hotspots, then continue reading this post. As someone smart has said, ‘its all around you, you just need to open your eyes and find it’. This thing goes quite well with finding free WiFi.
Most of us are not actually bothered much about it, or say we do not really try finding it. Sometimes scanning for WiFi networks using your default WiFi app won’t do. In this post I would be sharing some of the most amazing and fruitful ways to find WiFi hotspots for free.
3 Best Ways To Find Free WiFi HotSpots
1.) Use WeFi
Its not just about usi
 This is one of those possibilities that every Internet user think of that if there is a way we can integrate multiple email accounts to one single account. No doubt, such a thing will help you manage all your emails at one stop.
We would sharing a step by step guide which will let you combine multiple email accounts to one Gmail account. So, you need no log into your 5 different email IDs while you are checking your emails every day. All you need to is login to your Gmail account, and find all your emails getting diverted there.
Steps To Combine Multiple Email Accounts To One Gmail Account
The best part about this technique is that its not necessary for you to have all the Gma
This is one of those possibilities that every Internet user think of that if there is a way we can integrate multiple email accounts to one single account. No doubt, such a thing will help you manage all your emails at one stop.
We would sharing a step by step guide which will let you combine multiple email accounts to one Gmail account. So, you need no log into your 5 different email IDs while you are checking your emails every day. All you need to is login to your Gmail account, and find all your emails getting diverted there.
Steps To Combine Multiple Email Accounts To One Gmail Account
The best part about this technique is that its not necessary for you to have all the Gma
 Nothing is permanent in this cyber age. And Facebook is nothing different from any of these perishable things we have been talking about. So imagine you wake up one day and find that Facebook has been discontinued, then what about all your photos, videos and other Facebook data.
Yes, we are talking about easy ways to backup Facebook photos and data. Using these ways you can easily backup Facebook data. With the increasing popularity of Facebook, it is quite right to say that this social network has become a vital part of your lives.
And having your Facebook data backed up is not at all a bad thought. So check out the below methods, and see if any one work outs for you.
Nothing is permanent in this cyber age. And Facebook is nothing different from any of these perishable things we have been talking about. So imagine you wake up one day and find that Facebook has been discontinued, then what about all your photos, videos and other Facebook data.
Yes, we are talking about easy ways to backup Facebook photos and data. Using these ways you can easily backup Facebook data. With the increasing popularity of Facebook, it is quite right to say that this social network has become a vital part of your lives.
And having your Facebook data backed up is not at all a bad thought. So check out the below methods, and see if any one work outs for you.
 It’s easy to sit here and say that technology has always been great because of how fast it has evolved into what it is today. But the reality of technology is that there are way more failures than we might sometimes care to admit. Sure, there are devices and gadgets out there that are just stunningly great, but there are also plenty of innovations that don’t measure up to their reputation. This top 10 worst computers of all time infographic will shed some light on that.
I remember when I had a Spectrum and a Commodore 64 (and later on a Commodore 128) before I upgraded to an Amiga 500. It was heaven. But I can’t lie, there were problems with those computers. Comp
It’s easy to sit here and say that technology has always been great because of how fast it has evolved into what it is today. But the reality of technology is that there are way more failures than we might sometimes care to admit. Sure, there are devices and gadgets out there that are just stunningly great, but there are also plenty of innovations that don’t measure up to their reputation. This top 10 worst computers of all time infographic will shed some light on that.
I remember when I had a Spectrum and a Commodore 64 (and later on a Commodore 128) before I upgraded to an Amiga 500. It was heaven. But I can’t lie, there were problems with those computers. Comp

A security researcher and trained commercial pilot combined his interests and cooked up an exploit framework and Android app that can be used, at least theoretically, to hack a plane. That includes potentially gaining information about an aircraft's onboard computer, changing the intended destination, flashing interior lights, delivering spoofed malicious messages that affect the behavior of the plane, and, just maybe, if pilots don't manage to turn off autopilot and/or have difficulty with manual flight operation, crashing the plane. These are theoretical exploits demonstrated by Hugo Teso, a security consultant at n.runs AG in Germany, who gave a talk a [1] No more waiting to skip their ads! [2] Bypass adfly, adfoc, linkbuck, urlcash etc! Opera 1. Create a folder any where in your computer.for example C:\userscript 2. Copy this script file there.then rename it's from 118033.user.js to 118033.js 3. Open opera. Go to Settings > Preferences > Advanced>content>javascript options>select the folder created in step-1. Click "OK" and exit preference window. OR Install violentmonkey Then install this script Firefox download and install greasemonkey or 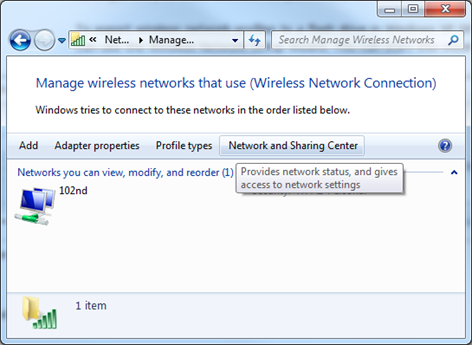 Windows 7 has got an intuitive GUI that makes you connect to any kind of Wireless network much easier than before. There is really no valid reason why you need or should use the command line to accomplish something that you can do the same through the GUI, other than, well, being cool. But anyway, let’s see how it works, all through the built-in netsh command.
To Connect
The simple line of command is
C:\>netsh wlan connect name=102nd
Connection request was completed successfully
Replace 102nd with your own profile name, and you are good to go.
A more formal syntax of connecting to a wireless network is something like:
netsh wlan connect ssid
Windows 7 has got an intuitive GUI that makes you connect to any kind of Wireless network much easier than before. There is really no valid reason why you need or should use the command line to accomplish something that you can do the same through the GUI, other than, well, being cool. But anyway, let’s see how it works, all through the built-in netsh command.
To Connect
The simple line of command is
C:\>netsh wlan connect name=102nd
Connection request was completed successfully
Replace 102nd with your own profile name, and you are good to go.
A more formal syntax of connecting to a wireless network is something like:
netsh wlan connect ssid
 The goal of most attackers, regardless of how they go about their business, is to steal user data. That could be in small, discrete attacks on individual users or it could be in large-scale compromises of popular Web sites or financial databases. The methods may change, but the aim is the same. In most cases, attackers first try to get some sort of malware onto user machines, as that’s the shortest route between them and your data. But if that isn’t feasible for some reason, another popular method of compromise is the man-in-the-middle attack. As the name suggests, this attack vector involves the attacker placing himself–or his malicious tools–between th
The goal of most attackers, regardless of how they go about their business, is to steal user data. That could be in small, discrete attacks on individual users or it could be in large-scale compromises of popular Web sites or financial databases. The methods may change, but the aim is the same. In most cases, attackers first try to get some sort of malware onto user machines, as that’s the shortest route between them and your data. But if that isn’t feasible for some reason, another popular method of compromise is the man-in-the-middle attack. As the name suggests, this attack vector involves the attacker placing himself–or his malicious tools–between th
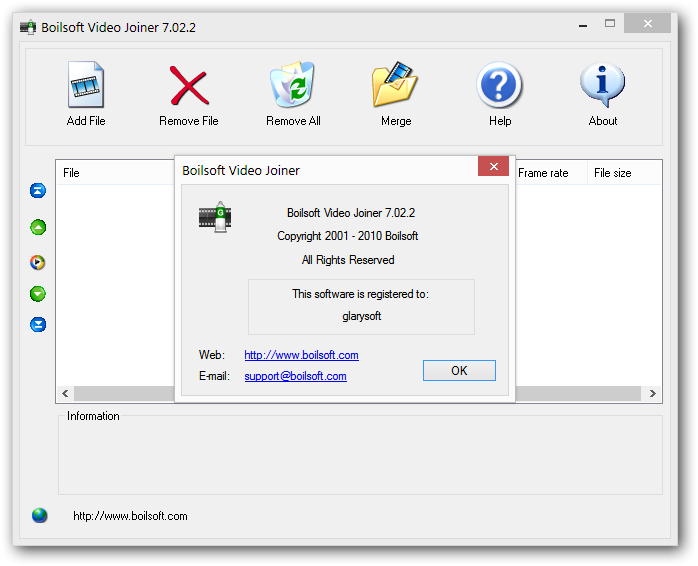
Boilsoft Video Joiner is a powerful video merger to join AVI, MPEG, MPG, VOB, RM/RMVB, 3GP, ASF, WMV, WMA, MP4, MP4A, MKV or FLV files, etc. to one "non-stop" larger file. Boilsoft video joiner provides you with Direct Stream mode and Encode mode to merge your videos more efficiently, and supports joining different format videos together at super speed. Join all kinds of video files into one large file – combine vacation, wedding and family videos into a much more enjoyable movie file Merge your favorite video files to another format such as 3GP, AVI, DVD, FLV, iPod, MP3, MP4, MPEG, PSP, RM, SVCD, VCD, VOB, WMV 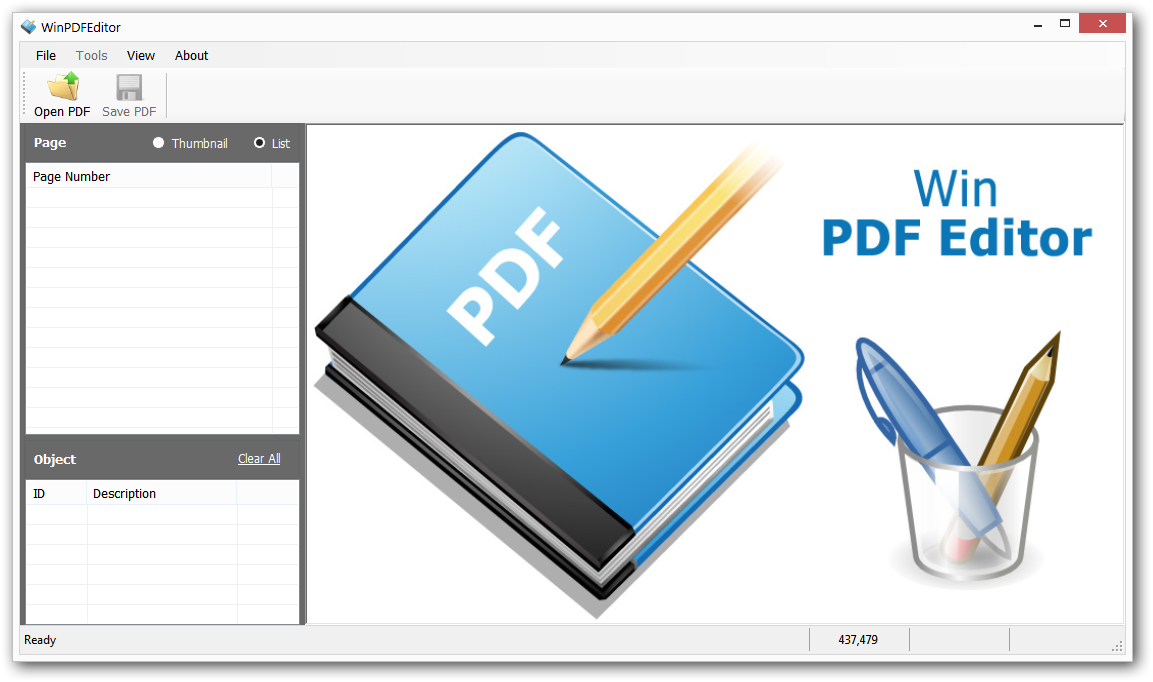
Edit PDF Easily: Add Text, Insert Images, Draw Shapes & Remove Unwanted Content. WinPDFEditor is a Windows PDF editing software product that lets you modify and edit PDF documentslike adding text, insert images, removing unwanted content, drawing lines and rotating PDF pages. If you write text on the PDF, you can change the text font, size, color and move it to anywhere you want on the page. After inserting an image into PDF, you can resize the image and move it also. If you find some words or images need to be removed, simply use the eraser tool to erase. Better than other PDF Reader applications, WinPDFEditor can per |
POPULAR COUNTRIES
SITE NAVIGATION
About Us
I
Media
I
Site Tour
I
FAQs
I
Why Us
I
Privacy Policy
I
Contact Us
I
Careers
I
Disclaimer
I
Add Free Business
I
Advertising Options
@Copyright 2013 My Infoline -Whole World At Your Fingertips
(This site in under beta version, please feel free to send your suggestion to improve this portal , and also write a email to us if you find any bugs.)
(This site in under beta version, please feel free to send your suggestion to improve this portal , and also write a email to us if you find any bugs.)

 India
India USA
USA Australia
Australia Spain
Spain Italy
Italy France
France Iceland
Iceland Brazil
Brazil Russia
Russia Nigeria
Nigeria Mexico
Mexico Iran
Iran North Korea
North Korea South Korea
South Korea Vietnam
Vietnam Egypt
Egypt China
China Turkey
Turkey